Category: Software
Software

Adept Expanding Its Technology in Utilities, Electricity, and Power Generation.
As our clients buy more power generation and electricity distribution companies we grow with them…

Inspections with Adept Enterprise ® on Candlewood Lake Connecticut for FERC Compliance.
The Adept Enterprise ® Shoreline Permit Management System is an enterprise software tool that provides…

Adept Land and Shoreline Permit Management Software
The Adept Enterprise Land and Shoreline Permit Management software system is a feature-rich solution designed…

Adept Virtually Eliminates Permit Processing Backlogs and Increase Inspections by 180%
Adept Technologies, the recognized leader in permit software innovation, helps Governments and Business Offices to…

Adept Enterprise® 20XX
Adept Enterprise® 20XX is the enterprise edge of the cloud, and/or cloud software platform that…
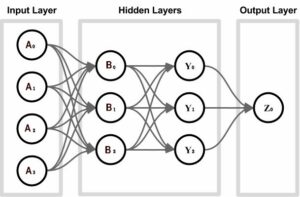
A.I. Artificial Intelligence
To understand how A.I. Artificial Intelligence functions are developed, we first need to understand the…
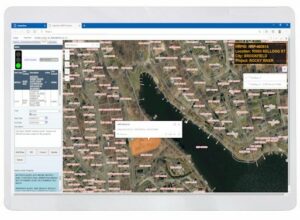
ESRI GIS Maps in Adept Enterprise®
We have gone live with many new server-side GIS features with ArcGIS Server integration with…

Adept Development History on Mobile Technology
In January 2003 Adept Technologies went Live with a revolutionary Mobile Inspections software system that…