Category: Network
Network
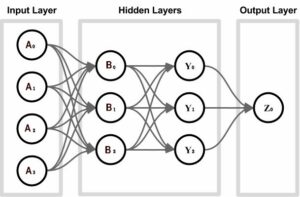
A.I. Artificial Intelligence
To understand how A.I. Artificial Intelligence functions are developed, we first need to understand the…

Adept Development History on Mobile Technology
In January 2003 Adept Technologies went Live with a revolutionary Mobile Inspections software system that…